2012年5月27日 星期日
Checkmate to Sandbox and Antivirus!
In the past few weeks, we noticed a rising number of malicious document can perfectly bypassed sandbox and all AV tools one could find on VirusTotal. Is it a zero-day exploit? No. It's simply a password-protected document. At the time of this blog, we have uploaded the sample onto VirusTotal, ThreatExpert, CWSandbox, etc, and confirmed our finding. A password-protected APT document seems like a no-brainier to beat all antivirus and sandbox on the planet.
Brandon (9bplus) also posted similar finding of these APT samples: "This document requires a password..."
Fortunately, XecScan is not bypassed. Without any update, XecScan detects them all.
The password-protected trick stops here. It is very encouraging to fans of XecScan, please continue enjoy our convenient, effective APT scanning service for free. ;-)
We observed that this wave of password-protected APT attacks mostly leveraged the recent MS12-027 CVE-2012-0158 in the form of word document (.doc), plus some PDF file and Excel spreadsheet (.xls), and yes all these documents require password to open!
Since sandbox-based solution have no idea what the password should be, their sophisticated virtual environments are completely useless, and no malware behaviors could be observed, no CnC IP, no callback traces, no nothing. Yup, a simple password easily reach the limit of sandbox technology! XD
How about antivirus solution?
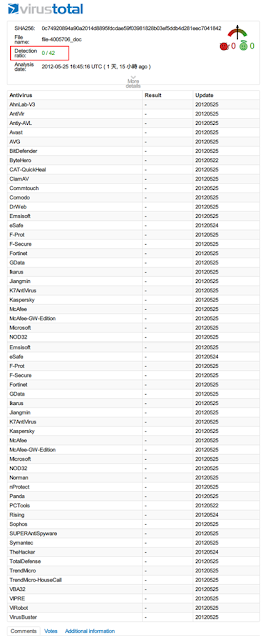
Existing antivirus detection rate is 0 for password-protected document.
As effective as zero-day exploit! Perfectly bypassed!
Big names like Txxxxxxxxx, Mxxxxx and Sxxxxxxx are no better.
Niche players like CWSandbox, F***Eye, etc all no luck.
As these samples now can be grabbed from VirusTotal, they should all start researching on it.
To fans of XecScan, we already foresee these at the time we designed our anti-APT technology last year, so we can detect these password-protected APT and can even diagnose the embedded malware.
MD5 : f297b8fafc6777249eb9e8f72f293969
File name : 退休俸改直撥入帳.doc
CnC : 74.179.56.228, 211.22.72.193
For security experts, this malware should be quite familiar, it's everywhere in Taiwan... ;-)
And with our data-mining and APT grouping technology, all these password-protected APT attacks seem to be launched by the same group of people...
---
Call for partners! XecScan now offers API for security experts and vendors to integrate our scanning capability into your offering. Please contact info@xecure-lab.com
A quick preview of the XecScan API response
訂閱:
張貼留言 (Atom)





沒有留言:
張貼留言