Last week a big cyber operation called DarkSeoul got massive attention on security community as well as on the whole world - South Korea under cyber attacks. Since then for almost a week we can't easily reach any Korean friends, and all sorts of news came out on the Web.
So here is our version. We first shared with CHROOT, HITCON, close partners, then you our readers.
Well, first, how bad?
Let's rereview the impacts on the day March 20th: (Thanks GD/Chroot for the summary)
Nonghyup Bank: 2,000 computers in 30 branches got affected, front desk activities suspended, more than half of ATM got shutdown
Shinhan Bank: 57 branches got affected, all database system crashed or stopped functioning, all transactions halted for 2 hours
Jeju Bank: unknown number of employees' PC got affected, all ATM got shutdown
KBS TV station: 5,000 computers got compromised, radio broadcasting stopped, official websites shutdown
MBS TV station: 800 computers got compromised, half of employees' PC shutdown, internet connections suspended, all using notebooks
YTN TC station: 500 computers got compromised, News broadcasting stopped
LG UPlus ISP: intranet computers got compromised, website got defaced
3 hours after the cyber attack, the military's INFOCON raised from 4 to 3 (normally it's 5).
Xecure Lab did some research on the malware and here's what we like to share.
[Disclaimer]
we are not involved with any official investigation done for South Korea, all information and samples are gathered from the web. And then we utilized our own forensics tool to put together our version of story. The first time we shared these information semi-publicly was to a close workshop hosted by HITCON(Hacks in Taiwan Conference) on 3/28 where officers from the government and people from the banks were invited to share lessons learned.
[Advertisement]
XecRay is an automated tool developed by Xecure Lab for APT-level cyber attacks. Our people highly rely on automation in detecting and countering malware, so that we're speedy enough for today's cyberwar.
[Story begins]
All information and inferences were based on the malware themselves, hopefully these released samples could tell us a bit what happens in Seoul.
Warning again, we conclude our story based on the samples we collected, it does not necessarily indicate what the truth is, please make your own judgement.
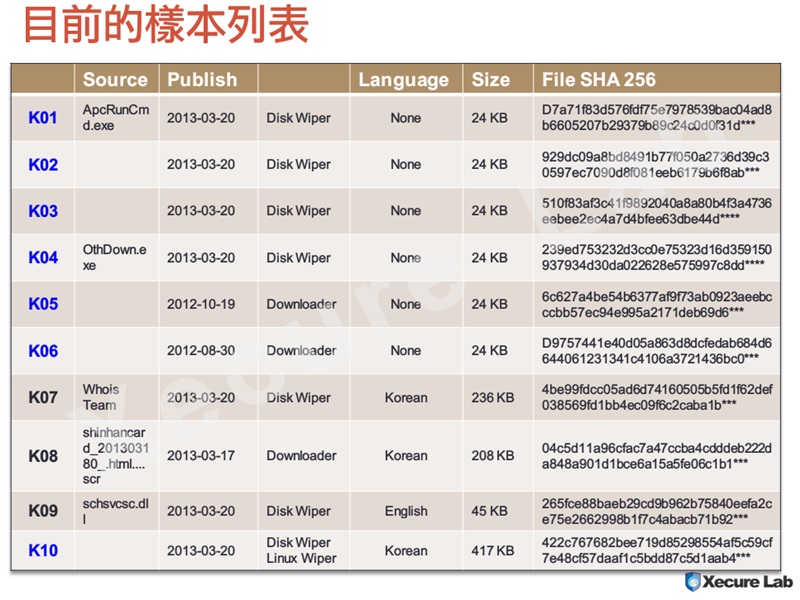
We spent several days in gathering all sorts of samples that might be the ones, and we concluded the following 10 samples are related:
Xecure Lab verified 10 samples that are related to DarkSeoul
The first batch that got released on the Web is K01~K04, and then Mila shared K05 and K06. We characterise Malware DarkSeoul base on the following attributes:
- has disk wiper functionality
- MBR string content of HASTATI, PRINCPES, PR!NCPES
- MBR access via \\.\PhysicalDrive
- sets critial section object
- JO840112-CRAS8468-11150923-PCI8273V
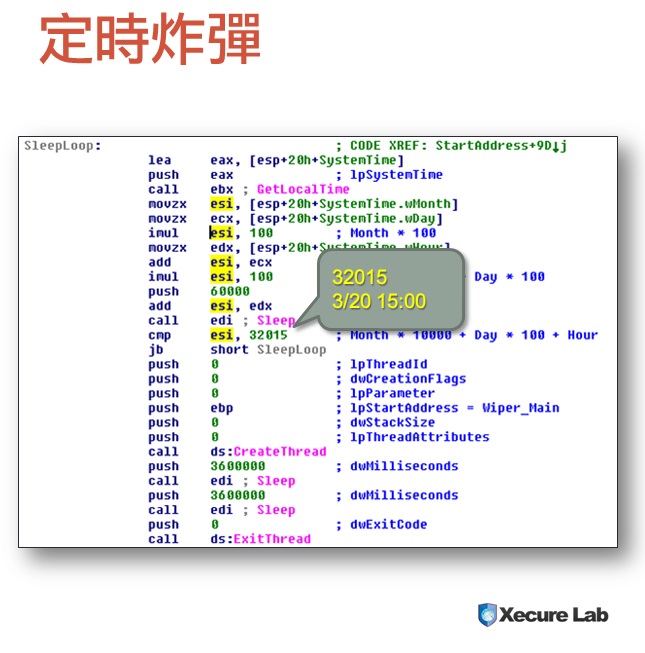
- has a time-bomb clock at 2013-03-20 1400 to 1500
- dump string related to "Whois Team"
- get rids of antivirus program
- AhnLab Policy Agent - pasvc.exe
- Hauri ViRobot - clisvc.exe
We have seen this timestamp in several malware samples, we believe it's a strong indicator of DarkSeoul.
disk wiper functionality, terminating antivirus functionality
Well, we have seen a lot of times, antivirus died first in cyberwar, and could even got abused to dispatch malware.... :(
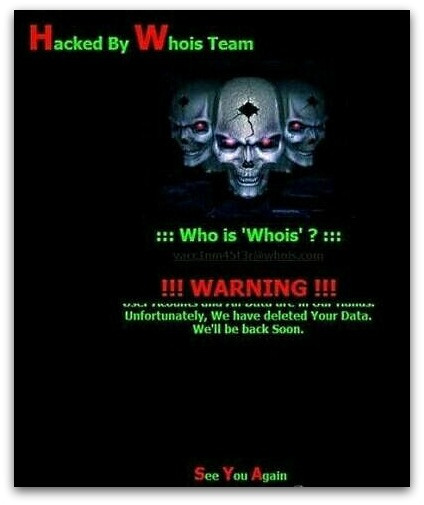
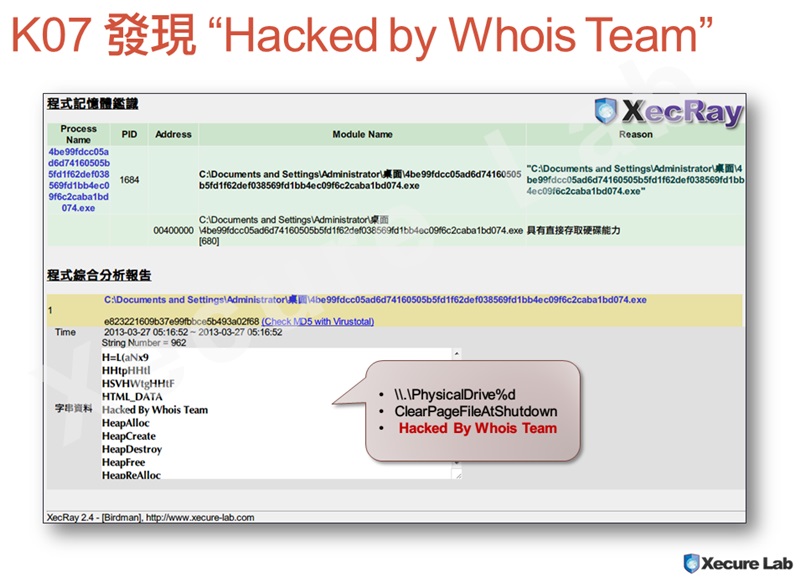
Whois Team
The sample K07 would drop an html file that highlights "Hacked By Whois Team". This is exactly the same defaced content on the LG UPlus' cyber security incident.
Defaced LG UPlus
K07 showed "Hacked by Whois Team" plus disk wiper functionality
(Reference http://www.f-secure.com/weblog/archives/00002531.html)
Some blogs said K08 is related with APT targeted emails, which could be possible, and in fact we have seen really a lot of targeted email attacks associating with APT intrusion. However, when we analyzed this sample K08, we still could not be tell if it's directly involved.
Though the filename has a substring of "shinhan" (the bank), we did not find any attributes of DarkSeoul in it. In addition, since the original email was not available, we couldn't tell if this targeted email was meant to hit employee or Shino's customers.
K10 is a freaking one, it's an enhanced version of K01, in addition to disk wiper functionality, it equips with the capability to search non-Windows platform and destoyed their data.
When K10 compromised a victim's machine, it will drop the followings files under temp folder:
- alg.exe (it's actually a disguised putty!)
- conime.exe (it's actually a disguised pscp!)
- AgentBase.exe (similar to K01~04, disk wiper)
- ~pr1.tmp (a shell script to erase your SunOS, AIX, HP-UX and Linux!)
Lastly, we found in K10 some environment info of the attacker such asE:\_O_\_N_\work\AutoServerCrasher\Release
\AutoServerCrasher.pdb, the _O_ could be a result of double byte issue! :)
Timeline of the attacks
Xecure Lab puts these malware togehter in a timeline based on their PE timestamp:
Samples K01 to K04 have the most publicity and all of their PE build time is 2013:01:31.
K06 and K05 though not directly related to DarkSeoul, but their binary structure are extremely similar to K01 to K04, we suspect the only difference is the payload.
Besides, the first seen date of K06 was back in 2012-08-30, at that time the filename jar_cachexxxxx.tmp, would this be a signal that the malware was planted while Java exploit gone wild last year? (our guess!)
- Gee... we didn't find any backdoor or Trojan, it's sooo disappointing for us, didn't get to see how fancy it could be (Flame is fancy though), but only disk wiper... -.-. Perhaps it's still in early stage of the whole investigation, and only a small portion of stuffs were released.
- The earliest attack probably happend as early as 2012-08-30, or as late as 2013-01-31. The whole cyber operation took several month to launch the D-day attack, this is a typical kind of advanced persistent threat attack。
- Who did it?
Everyone is asking. But, based on the sttufs we have, we can't tell. There is no IP or domain to infer or to make a wild guess, besides, these samples are all not backdoors. They are attacking weapons. In alienvault's blog, they mentioned 103.14.114.156 were involved, however we think that shouldn't be the case, at least it's not DarkSeoul.
We hope more stuffs got released, so that the whole security community can get more insights out of this national-level cyber attack in practice....
[Story ends]
[Story ends]
It's in times of cyberwar!
And some countries had been hit badly, are we ready?... XD
Birdman, Benson
Xecure Lab
-----
Higher management: If this APT happens in Taiwan, what could happen?
Xecure Lab: Ah? Didn't that happen several times? And actually most people feeling no pain, so no worrrrrry, sir. T_T
----
HITCON 2013, 7/19~20, welcome to gossip about security!
http://hitcon.org/2013/
-----
Higher management: If this APT happens in Taiwan, what could happen?
Xecure Lab: Ah? Didn't that happen several times? And actually most people feeling no pain, so no worrrrrry, sir. T_T
----
HITCON 2013, 7/19~20, welcome to gossip about security!
http://hitcon.org/2013/







沒有留言:
張貼留言